As technology continues to advance, it has significantly transformed our lives for the better. From smart devices that help us organize our schedules to social networks that keep us connected, we are increasingly surrounded by technological innovations. At the heart of this convenience lies a trade-off: our privacy. As we rely more on these technologies, we become vulnerable to risks such as identity theft and unwarranted surveillance of our personal lives. Below, we explore 19 hidden dangers associated with technological advancements that threaten our privacy.
Data Collection from Smart Devices

Laptops, desktops, tablets, cars, smart home appliances, and wearable devices also gather information all day. Each time you talk to them, they document small information and incidences, even though, at times, you feel that they are unfocused. As it aims to enhance the services, it also means that tech firms have access to people’s messages, daily routines, and even confidential details.
Location Tracking
Every time you launch an application on your smartphone, it will request permission to access your GPS. Your maps, weather apps, social media, or shopping apps all make use of GPS data to give your recommendations. But that same data can also be sold to advertisers or, even scarier, be used by hackers who can then follow you throughout the day.
Insecure Wi-Fi Networks

Even though Wi-Fi networks are widely available and convenient, they can be dangerous if not properly secured. When you use public Wi-Fi to access services, people around you can easily hack into the data you transmit and receive, including passwords and credit card details. Not even your home Wi-Fi is safe if it is not set up correctly.
Social Media Platforms

Facebook, Instagram, X (previously Twitter), and many other social media services are built on the information provided by users. Every scrap of content, every comment, and every like is watched, leaving a perfect record that, in turn, can be exploited for advertising. At its worst, your identity might be sold to other people or companies, or your information will be leaked if the database gets hacked.
Facial Recognition Technology

The use of face detection is increasingly being adopted on phones, security systems, and even in public places. Whereas it may appear relatively easy, it is also an invasion of privacy. Employed by governments or private corporations, this technology follows your every step, and when in the hands of criminals, consider identity theft.
Data Breaches

Large corporations that gather large amounts of consumer data are attacked regularly. That is why, through data breaches, you can end up losing your financial details, passwords, and even social security numbers. Your data, once stolen, can be sold on the black market and used for other vices, including identity theft.
Targeted Advertising

Have you ever searched for a specific product using an internet browser and then visited your Facebook account a few hours or even days later only to find that advertisements for the product you searched for suddenly appeared in your feed? This occurs because organizations monitor your internet activity and personal behavior to market goods and services to you. Despite appearing harmless, it entails sharing your data across the various worldly platforms you use without consent.
IoT (Internet of Things) Devices
It is now possible to buy a refrigerator that can inform you when supplies are low, a thermos that can monitor and display the temperature of its contents, and other devices that alert you when the temperature changes. However, several of the above gadgets have no significant security measures and hence can be easily attacked by hackers. Once hijacked, they can be used to break into your home or network.
Cloud Storage Vulnerabilities

The growth in using cloud storage to save files and data has made it easier but with various dangers. Your files can be opened and viewed by individuals who have no right to do so if they have gained access to the files. Worse still, some unscrupulous cloud providers may analyze your data for profit by stripping away its sensitive details before using it.
Third-Party Apps

Whenever people download applications, they tend to grant the application permission to access their contacts, photos, location, and others. Some of these apps may be selling your data to third parties or are insecure, leaving you an easy target for cybercriminals. Always review the permissions an app requests and consider whether they are necessary for the app to function properly.
Email Phishing Scams

Despite these developments, there is still a high possibility of carrying out phishing scams. Phishing is exercised by sending a fake e-mail that forces the receiver to enter a password or account number. Sadly, these attacks have become even more subtle and are much more obscure by present-day standards.
Deepfakes and AI Manipulation

The generation of fake videos and fake audio, known as deep fakes, is getting easier as AI technology moves forward. These can be employed for electoral fraud, extortions, or to feed the creation of fake news, threatening your reputation and data.
Wearable Technology

Modern wristbands and smartwatches can harvest views of health data – pulse, training, slumber, etc. This data can then be sold to other therapies or insurance service providers to be used to either increase premiums or even to decline to insure.
Virtual Reality (VR) Privacy Risks

Privacy concerns are growing as virtual reality gains popularity for gaming and other uses. VR devices can track information such as head and heart rate, user preferences, and behavior, allowing companies to gather detailed profiles of individuals.
QR Code Scams

Although QR codes offer a quick way to access information, they also come with risks. Scammers can create fake QR codes that direct users to phishing sites or download malware onto their devices, putting personal information at risk.
Spyware and Malware

Spyware and malware have existed for many years but have been upgraded according to technological improvements. Many of them could be accidentally downloaded into your device, giving hackers control of your keyboard, camera, or personal information.
Smart Home Devices
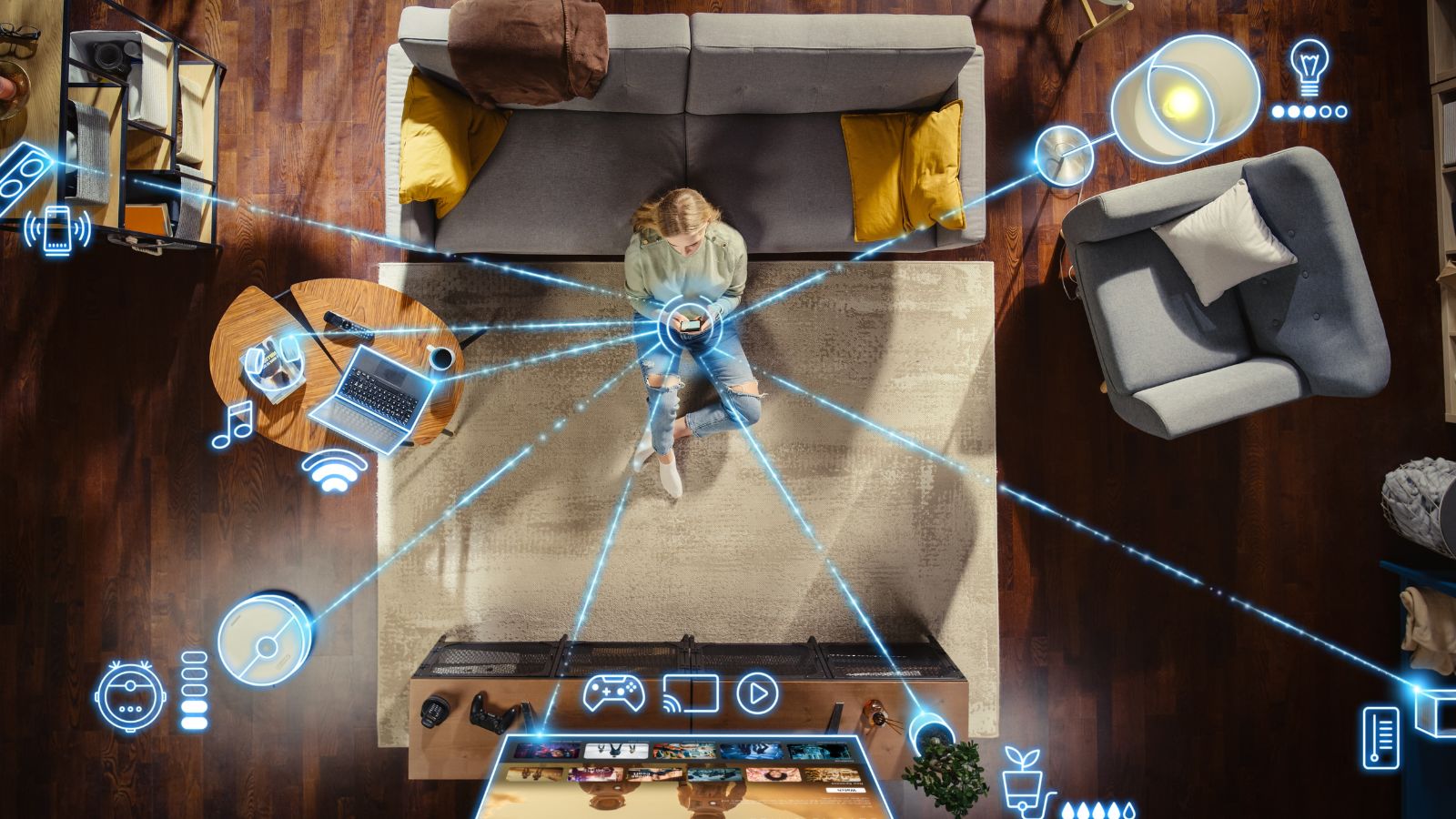
A smart home alarm system, smart doors, and smart bulbs are vulnerable to hacker attacks, and thus, they make your home unsafe. Some individuals can see what you are doing through your cameras, open or unlock your doors, or even control your lights, thus endangering your security.
Online Banking and Payment Apps

Online banking facilities like PayPal and Venmo somehow make some transactions efficient and comfortable, although they are vulnerable. You lose control of your account and can face identity theft or any other form of financial scam.
AI-Powered Surveillance

As technology advances, so do the threats to our privacy. While AI-powered devices offer convenience and improve various aspects of our lives, they also introduce significant risks. Identity theft is a serious concern, and we must recognize our role in safeguarding our personal information by being more vigilant and taking necessary precautions. It’s clear that the rise in technology usage brings many hidden threats, so we must exercise extra caution regarding the amount of personal information we share.
Conclusion

In conclusion, technology’s rapid advancement brings remarkable benefits and significant risks to our privacy and security. While these innovations enhance our daily lives, they also expose us to potential dangers, including identity theft and data breaches. It’s essential to approach these technologies with caution, being mindful of the personal information we share and with whom. By staying informed and vigilant, we can better navigate this complex digital landscape and protect ourselves from the hidden threats that accompany technological progress.
18 Reasons Why People Are Leaving Florida in Masses

Exploring factors that impact the desirability of living in Florida, this list delves into various challenges shaping residents’ experiences. From environmental concerns like rising sea levels to economic factors such as fluctuating job markets, these issues collectively contribute to a nuanced understanding of the state’s appeal.
18 Reasons Why People Are Leaving Florida in Masses
